Tip: Use Your Microsoft Account Properly
- Paul Thurrott
- Feb 01, 2024
-
10

Microsoft created the Microsoft account (MSA) as an online identity that its customers can use to sign in to Windows, Office, Outlook.com, Xbox, and many other connected products and services. In many cases, it’s required to access specific solutions or their full feature sets. But the benefits are obvious. Having a single account across these solutions simplifies matters, and it enables the deep integrations that we all enjoy across the ecosystem.
It’s impossible to overstate how important it is to properly secure your Microsoft account. And that’s true whether you use this account sparingly, perhaps just to play games on Xbox or for a secondary email account, or use it as your main online identity. Securing this account isn’t difficult, but security is a daunting topic for most of us. And while it’s easy to use that as an excuse to procrastinate or even ignore this task entirely, please don’t do that. Put aside a half hour and just get it done.
Windows Intelligence In Your Inbox
Sign up for our new free newsletter to get three time-saving tips each Friday — and get free copies of Paul Thurrott's Windows 11 and Windows 10 Field Guides (normally $9.99) as a special welcome gift!
"*" indicates required fields
Once your MSA is properly secured, you can seamlessly and securely access whatever Microsoft platforms, apps, and services you want. Fans of the Microsoft ecosystem will typically want to do that quite broadly, while others will mix and match between other solutions made by other companies, many of which have their own online accounts (that also need to be properly secured).
I fall into that latter camp: My Microsoft account (MSA) is one of my two core online identities—the other is my Google account—and I use it to sign in to Windows, to access my Microsoft 365 Family and Xbox Game Pass Ultimate subscriptions, for OneDrive cloud storage (which houses the main/master version of my photo collection), and for some identity verification via the Microsoft Authenticator app on my mobile devices.
But you could also use more of Microsoft’s solutions than I do.
For example, I use Microsoft Authenticator solely for Microsoft various Microsoft accounts (I have several, including a commercial Microsoft 365/Entra ID account), but I turn to Google Authenticator for other accounts because it seamlessly syncs all of its contained accounts to the cloud, making it simpler to move between phones. (This won’t be an issue for most people, plus you can back up and recover Microsoft Authenticator stored accounts.) Using just a single authenticator app makes sense, and Microsoft Authenticator is an excellent choice.
Tied to Microsoft Authenticator is this notion of password management. I use a third-party password manager and install its app on mobile and its extension in the browsers I use in Windows. But if you want a more seamless experience, you can use your MSA for password management and make Microsoft Authenticator your autofill provider on mobile: In addition to its account verification capabilities, Microsoft Authenticator integrates with your MSA back-end.
If you use Microsoft Edge in Windows, other desktop systems, or on mobile, you get that password integration automatically. But if you use Chrome or some other web browser in Windows (or other desktop systems), you can install the Microsoft Autofill extension to get that integration there as well.
So let’s step through this.
You’ve properly secured your Microsoft account, right? That’s job one and a requirement for anyone who will use this account as the center of their digital lives.
You sign in to your Windows PC(s) with your MSA, so Microsoft requires you to configure a PIN. This simplifies signing in, but it’s also an additional layer of security, something that is different from and additional to your password. But here’s something many people don’t know: For the best security, you should use a different PIN to access each of your PCs, phones, and other devices. As with passwords, you are not supposed to reuse PINs. Reuse is a key security mistake.
If your PC provides Windows Hello biometric authentication—the ability to sign in to the PC using facial or fingerprint recognition—you should enable one or both and use one instead of the PIN. This happens in the Settings app, in Accounts > Sign-in options.
(And if your PC supports presence detection, I recommend enabling that as well so that your PC wakes up when you approach and automatically locks when you step away. This functionality is available in Windows 11 now, but I still get PCs to review that use custom configuration software from the PC maker. So you may need to hunt around if you know your PC supports this feature.)
Signing in to your PC with your PIN, face, or finger is secure, and so Windows passes through that identify verification to other apps and services, including such things as OneDrive (cloud storage with file system integration), Microsoft Edge (web browsing), Widgets (widgets and news feed), Copilot (AI services), Outlook (email, calendar, contacts, and to-do’s), Microsoft Office (with ties to your Microsoft 365 subscription perks if available), and Microsoft Store (apps, games, movies, and TV shows), plus many more. This passthrough typically lasts for the duration of your session, which ends when you log out or lock the PC. But you may need to reauthenticate midstream occasionally in certain circumstances. For example, if you open Microsoft Edge and visit the Microsoft account website, you won’t typically be asked to reauthenticate. But if you access its security dashboard, you will be. As with your initial sign-in to Windows, Windows Hello makes this easier and more seamless.
Windows 11 also lets you save passkeys locally using the secure storage in your PC’s TPM security chip. Passkeys are not saved to your Microsoft account, though they will be eventually as that standard evolves. But they do utilize your secure Windows Hello PIN or biometric authentication, which makes them easier to use for two-step authentication than an authenticator app, because that happens right on the PC and doesn’t require a second device. Passkeys are compatible with all major web browsers, including Microsoft Edge, which is included in Windows.
Speaking of which. If you use Microsoft Edge in Windows, you should configure that correctly because this web browser is designed to secretly track your activities online and sell your personal data to advertisers. But either way, Edge integrates with your MSA, and, among other things, it syncs a wide range of settings through that account. You can see and configure this in the browser settings in Profiles > Sync.

And if you are syncing all of those settings, as I suspect most Edge users do, then you are also probably also storing passwords (really, the username and password for each online account), payment information, and other personal data for your other online accounts with Edge. Which means that you’re using your MSA as a password manager. I wish Microsoft had a single name for this capability—Google logically uses the name Google Password Manager everywhere—but it doesn’t. In Microsoft Edge, it’s called Microsoft Wallet, and what you need to know is that any passwords you save in Edge are saved in your Microsoft account and can be made accessible in other web browsers and on mobile devices, where they can be used to autofill on the web and in apps.
If you were previously using a different password manager—whether it’s built into another web browser or a standalone solution—you can of course import your passwords, along with other data, using Microsoft Edge. You can also use the Password check feature in Edge to see whether any of online account credentials have been leaked online. This interface also reports which of your online accounts use weak or reused passwords, along with a link next to each entry so you can change them. Do so.
If you’re all-in on Microsoft but still use Chrome or a different Chromium-based web browser, you can install the Microsoft Autofill extension, as noted earlier, and retain your MSA as your password manager. (There’s no way to do this on Firefox, sadly.) As with Edge, this add-in helps generate new passwords and can manage your payment info and addresses too. In fact, the Microsoft Autofill settings interface is nearly identical to Microsoft Wallet in Edge. (There’s no Password check feature, unfortunately.)
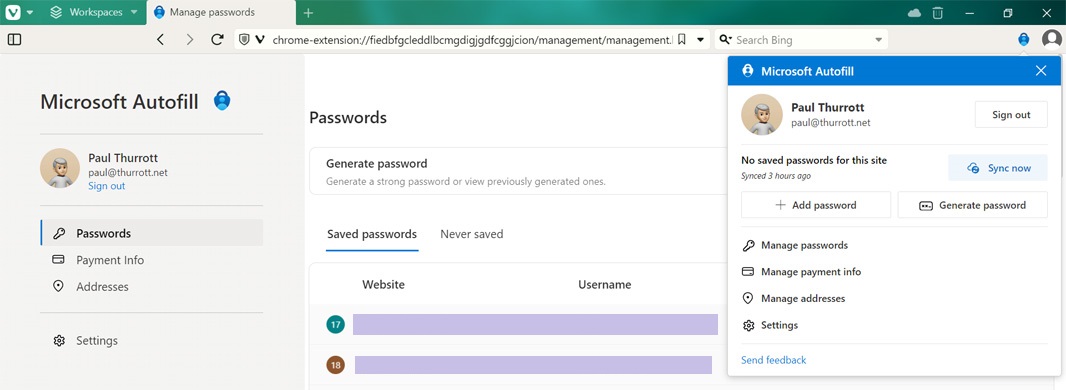
If you use Microsoft Authenticator on mobile for account verifications, you can configure that as your autofill provider as well. You’re prompted to do so when you first install the app, but you can configure it later in Microsoft Authenticator settings.
On Android, just enable the “Set as autofill provider” option and then choose “Authenticator” (with the blue shield icon) in the Autofill service screen that appears.
On the iPhone, Apple makes things more complicated. Open Authenticator settings, then “How to Turn on Autofill,” “Open Settings,” and “Password Options.” In that last screen, select “Authenticator” (with the blue shield icon) under “Use Passwords and Passkeys from:”. Be sure to also uncheck “iCloud Passwords & Keychain” or an Authenticator panel will pop up, letting you know that you have to take one more step. (Again, I’m assuming you’re all in on your MSA here.)
Be sure to use biometric authentication on your mobile device to access Microsoft Authenticator. What you can use will vary by phone. On iPhone, you can use Face ID or Touch ID, depending on what your iPhone has. On Android, many facial recognition systems aren’t secure enough to use for Authenticator, so you may need to use your finger. My Pixel 8 Pro supports facial recognition here, for example, but my Pixel 6a does not.
And there it is: You’re living la vida Microsoft. There are worse paths to choose.